On-Demand Outsourcing BPO Services for Healthcare Providers With 24/7 Coverage!
Save up to 70% on staffing costs!
Browse Specialty Staffing ServicesEmerging Technologies for Contact Tracing during COVID-19

Author: Ishika Choudhary
Abstract:
Currently, the breaking down of barriers to global health sector, the COVID-19 pandemic has transformed the worldwide health community’s acceptance with the utilization of digital health technologies, that facilitate pandemic strategy and chargeable for forming a bridge for the health sector which fulfills the current need for throughout area unit troublesome which were inaccessible manually. Massive knowledge have facilitated COVID-19 preparation even the tracing of individuals, which has unfolded the infection, in many countries. The perceptive of initial reactions in several quarters, it looks that the COVID-19 area unit is unlikely to bring substantial modification to the conception of development cooperation policies, even among the health sector, from the event partners’ perspective. Indian government launched the Aarogya Setu app or say “Bridge to Health sector” app with this emerging technology contact tracing at a mass scale with one hundred million downloads since April, which has remodeled the contact tracing. This COVID-19 crisis has started the trend of using a pandemic tracing app, moreover, numerous advanced techniques are ready for an epidemic of these proportions. Activities analyzed around the world to produce inbound contact tracking applications can be ready soon if they are evaluated prior to the pandemic’s commencement.
KEYWORDS: global health sector, digital health technologies, COVID-19 pandemic, Aarogya Setu, contact tracing app.
INTRODUCTION:
Several of the applications stood out in the lack of the same strategy used by authorities, policymakers, and developers. As a result, they differed in terms of performance as well as the underlying technology. Several nations throughout the world provide free COVID-19 contact tracing applications. As a result, multiple applications utilizing various approaches for contact tracing and infection news have emerged. In the clinical application of molecular diagnosing technology, it is necessary to combine morbific biology, medicine, and other associated detection technologies, advocate the combination of multiple technologies, confirm how they complement one another, improve practicability, and improve the power of quick and correct diagnosing and medical diagnosis medical diagnosis. Several apps are now being developed or planned, with official government assistance in specific areas and jurisdictions. Many frameworks for developing contact-tracking apps are being created. Privacy concerns are highlighted, particularly in relation to systems that are supported in tracking the geographical position of app users. COVID-19 apps are mobile code applications that may be used to track digital contacts during the COVID-19 pandemic, the means of identifying people (“contacts”) who may be in contact with an infected individual.
As countries open their economies, several health consultants are concerned about a “second wave,” or resurgence, of COVID-19. To prevent a second wave, public health consultants are advocating that nations implement contact tracing, which entails tracing all people who have recently acquired contact with someone who has tested positive for COVID-19 and taking business steps to isolate those people. The danger to non-public privacy was serious enough for Google and Apple to work on an API that public health organisations’ developers will utilise to construct app-based contact tracing solutions. This contact tracing API, dubbed the Exposure Notification API by Google and Apple, is intended to protect user privacy and security.
Less invasive solutions include using Bluetooth signals to log a user’s proximity to other mobile phones. On the tenth of the Gregorian calendar month of 2020, Google and Apple announced that they will add functionality to support such Bluetooth-based apps directly into their golem and iOS operating systems. India’s COVID-19 tracking app Aarogya Setu became the world’s fastest growing app, surpassing Pokémon Go with fifty million users in the first thirteen days. Contact-tracing, a disease management technique that relies on patients’ memories of their travels in the past, identifies persons they may have infected so that they can be quarantined. [1]
CORONAVIRUS PANDEMIC: Emerging Technologies Addressing Major Challenges:
Our Innovation Analysts employed a data-driven, bottom-up analytical technique to identify 4,830 startups and emerging enterprises working to reduce or control the spread and consequences of the new coronavirus.

Fig.01: Five Apps for Older Adults during COVID-19
Some of the primary difficulties that these emerging technologies address include:
- Preventing people from being sick or spreading the virus. Remote health monitoring, autonomous medical aid, and contactless temperature guns all help to slow the spread of the virus.
- To provide further assistance to society’s most disadvantaged groups. Virtual doctor visits, chatbots, and online patient engagement technologies, together with remote diagnostic solutions, assist reduce the number of people who need to attend a hospital.
- To preserve normal public safety and health amid a ferocious sickness. Support tools and mobile applications for caregivers, use of drones to carry medical supplies, and specialised isolation units all help to keep frontline workers from being infected.
- To prevent coronavirus transmission in the community. Shared streaming services, remote employment, and the treatment of loneliness, stress, and anxiety all change how individuals and physicians manage their mental and physical health during incarceration.
Notification of Exposure:
The (Google/Apple) Exposure Notification (GAEN) system, formerly known as the Privacy-Preserving Contact Tracking Project, is a framework and protocol specification established by Apple Iraqi National Congress and Google to assist digital contact tracing during the COVID-19 epidemic. When used by health authorities, it supplements other old contact tracking approaches by automatically working encounters with alternative notification system users who use their robot or iOS smartphone. Exposure Notification is a distributed reporting technique built on a combination of Bluetooth Low Energy technologies and privacy-preserving encryption. It’s utilized as an opt-in feature in COVID-19 applications created and released by approved health authorities.
Table.01: Pandemic preparedness and response programs utilizing digital technologies.
Technical specifications: Typically, digital contact tracing systems are responsible for two key tasks: encounter work and infection coverage.
To conduct encounter work, the system sends the following messages to nearby devices using the protocol to obtain encounters with humans. The communications below contain unique IDs that are square measure encrypted with a secret daily key controlled by the causative device. These identifiers are updated every 15–20 minutes, as well as the Bluetooth mack address, to prevent unscrupulous third parties from following consumers through perceived static identifiers over time.
A random variety generator was used to produce the sender’s daily coding keys. If a person is infected, the last fourteen days of their daily coding keys are uploaded to a central server,wherever it’s then broadcast to all or any devices on the network. Individual app developers design the approach for daily coding keys square measure sent to the central server and disseminated. A health official must request a one-time verification code from a verification server, which the user enters into the encounter work app, according to the Google-developed reference implementation. This results in the app receiving a cryptographically signed certificate, which is used to allow key submission to the central coverage server. The initial applications had limited acceptance and were squarely constrained by their lack of Apple-Google technology. A major problem is that applications might register a staggering number of erroneous contacts. Concerns about privacy may restrict app adoption and render them useless. Healthcare providers should make full use of whatever suggestions are made that square measure obtainable to avoid wasting lives and confine the unfold of the virus. [8]
Individual A’s contacts (and all persons using the app) are obtained from GPS co-localisations with other App users, which are reinforced by scanning QR-codes placed on high-traffic public utilities when GPS is just too imprecise. Individual A orders a SARS-COV-2 test (through the app), and their positive test result generates a second notice to those with whom they are in close touch. Individual A should be isolated, and their contacts should be quarantined, according to the app.”
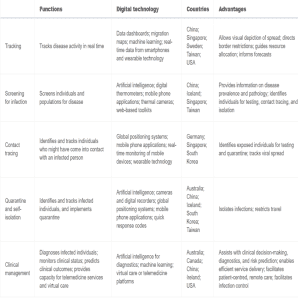
Figure 02: A diagram of app-based COVID-19 contact tracing.
Among the most prevalent aspects of the applications are live maps and updates of confirmed cases; time-based location-based notifications; means for surveillance and dominant home isolation and quarantine, direct reports to the government, and self-reporting of symptoms; and instruction about COVID-19. Some more sophisticated services include self-assessment of daily physiological state; monitoring of critical parameters such as temperature, heart rate, atomic number 8, and force per unit area using Bluetooth-enabled medical equipment. We discovered that thirty of the fifty apps require authorization to access various aspects of users’ mobile devices. Access to contacts, photos, media, files, location information, the camera, the device ID, decision data, the wireless fidelity affiliation, the electro-acoustic transducer, full network access, Google service configuration, and the ability to change network property and audio settings, to name a few examples. Furthermore, some applications specifically indicate that they would collect data on the user’s age, email address, sign and communication code; the device’s location, unique device identifiers, mobile scientific discipline address and in-operation system; and the types of browsers used on the mobile device.
A perplexing discovery is that just sixteen of the fifty applications declare that the user’s data will be generated anonymously, encrypted, and safe, and would be transferred online and published primarily in aggregate format. Our data cover a variety of government-issued COVID-19 tracing apps from both developing and developed nations. Twenty applications from our sample were published by governments, health ministries, and other similar official sources, which is quite concerning. While the US government is not currently asking voters to download any tracking applications, there are apps in the Play Store produced by North American country health care providers (Sentinel health care, 98point6, and Health Lynked) that offer comparable functions. What is unclear is if any of these the data the info the data collected are protected by any laws or laws like the insurance immovability and answerability Act or electronically protected health information. [2]
Some governments, like China, Israel, Singapore, and Asian countries, have produced the following applications to combat the epidemic, and numerous new industrial apps have been released since the outbreak began. In this article, we will look over fifty applications available on the Google Play Store that are designed exclusively for COVID-19. As key health care players (healthcare suppliers, pharmaceutical corporations, and med techs alike) explore new methods of working, as well as increase robustness during “peacetime,” this increasingly digitalized reality may compel a paradigm change inside the healthcare system. [3, 4]
Figure 03: COVID-19 app data dashboards.
In comparison to prior infectious-disease outbreaks (for example, the 1918 ‘Spanish flu’ pandemic and the 1957 ‘Asian flu’ pandemic), the COVID-19 disaster is taking place in a far more connected and digital environment. Several governments are calling for a comprehensive police probe to stop the spread of COVID-191. The digital police inquiry is also the most efficient way to control the spread of the irruption, but privacy rights should be considered both now and as the crisis progresses. [5,6,7]
Aarogya Setu: Aarogya Setu is a centralized app that has been launched throughout the Republic of India. On May 6, 2020, the code for his or her automaton app was released (iOS and server codes are still unavailable). This software collects location knowledge (GPS coordinates) and self-assessment knowledge in addition to PII and contact information (responses provided by a private to the self-assessment test). It uses knowledge analytics on the collected data to determine how many positive instances are within 500m to 10km of a user’s present location. If users are COVID-19 positive or fail the self-assessment test, they will transfer the trace knowledge. Unlike other applications, the government of India has made it mandatory for all government officials and citizens residing in disease containment zones to download the Aarogya Setu app.
Figure 04: COVID-19 app target consumers in India. [11]
App Abuse: The goal of this form of assault is to fool the monitoring app using data obtained via incorrect app use. A recent Google Maps experiment is reported, in which a person was carrying 99 cell phones along an empty road, and Google Maps replied by indicating significant traffic. Similarly, monitoring software cannot tell whether a phone is being held by its owner, another person, or a puppy trotting about the park. To avoid these actions, new safeguards can be implemented, such as leveraging numerous existing sensors on the phone to monitor activity or do gait recognition. Capturing bigger volumes of speech or personal knowledge, on the other hand, may result in less privacy safeguards. [12.]
Common User Issues:
COVID-19 monitoring applications have been extensively embraced in a number of countries; for example, over five million people downloaded the CovidSafe (AU) app during its initial release in Australia. Similarly, downloads for the Aarogya Setu monitoring app in India surpassed 114 million. This app is used as a measure of consumer satisfaction. However, we believe that this is not a sufficient criterion for determining the impact or usefulness of a contact-tracing tool. We frequently require further information, such as the number of closed contacts identified by an app’s data and the accompanying false positive/false negative rates. Typically, health professionals use manual contact tracing in conjunction with app knowledge to identify closed contacts for a known case. There are three unique possibilities in this regard: a) The app’s contacts correspond exactly with the manual tracing method; the software has fulfilled its goal, and hence the knowledge is used as confirmation. b) The contacts recognized by the app have a square measure advantage over those known by the manual tracing procedure; the software has fulfilled its goal and shown its usefulness. c) The app square measure contacts but not those known by the manual tracing procedure; the app’s performance is unclear. However, as of this writing, there is no openly market knowledge that will be used for impact analysis and assessment of the efficacy of any of those applications, and several concerns linked to the usage of such contact tracking apps have been identified. We have the propensity to discuss difficulties linked with user knowledge privacy and security in Sections III and V. In this part, we tend to address a number of the additional issues from user’s perspective.
A.) Battery Usage B.)Consent Withdrawal C.)Transparency
A.)Battery Consumption: Excessive battery consumption may be a recurring issue for mobile apps. Several aspects influence mobile battery consumption, such app processor use, frequency, the extent of knowledge management, and therefore the diversity of messages altered, and so on. Most tracing applications accept the BLE communication protocol to exchange data with peers, however some apps communicate with servers using standard cellular or wireless local area network connections. Communication with the server, on the other hand, is based on ancient secure application protocols, such as HTTPS. The number of data exchanges with the server is thought to have the greatest influence on battery utilization for these protocols. Battery usage is also hampered by the execution side since an app running in the forefront requires more power than an app that runs within the background. These style choices are often determined by the OS’s compatibility with certain programs. As an example, CovidSafe and Trace Together IoS programs have these reported issues when operating in the background. Google and Apple, the two largest smartphone operating system providers, have collaborated to provide exposure notification Apis that enhance tracing application interaction with the operating system. These Apis square measures are anticipated to improve app development and reduce power usage. [13,14]
- Consent Withdrawal: Consent withdrawal refers to a user’s ability to refuse to participate in knowledge sharing. Consent withdrawal ensures that consumers can remove their knowledge or disappear from the tracking app system whenever they desire. At various phases of the app’s functioning, we tend to consider the consent withdrawal mechanism next.
A phase of data collection: Because encounter information is only held on user devices for a certain length of time (for example, twenty-one days), uninstalling an app entails the removal of all encounter knowledge from the device in a single shot without transmission to a server. Furthermore, for the centralized design, app deactivation is considered to result in the erasure of all personal knowledge gathered during the registration step. However, because the encounter information sharing occurs on a regular basis, various active users will have encounter messages/chirps stored in their devices for twenty-one days. Similarly, if a user withdraws approval for the hybrid design, and deletes the native knowledge, PETs generated mistreatment of their broadcasted EphIDs would stay within the native storage of contacts.
As a result, the server evaluates this information and alerts shut contacts. Because this contact data is not sent to the closed contacts, the server will simply delete the submitted data because it has already been utilized. In terms of systems, it is theoretically conceivable to delete such knowledge while providing a receipt or feedback to the user. If the infected user requests knowledge deletion, the server will release the hold on knowledge; however, it is unclear if the seeds that have already been distributed to additional devices are frequently promptly removed from these devices.
End of a pandemic: Most authorities in charge of tracking applications have said that the app knowledge gathered would be destroyed after the system is deactivated at the end of the pandemic, referred to as the sunset clause unless a user asks for explicit early release of their hold on knowledge. However, the phrase “end of the epidemic” may be too broad. Proposals such as DP-3T feature an automated system for removing knowledge from the server and hence the customers after a certain quantity is reached. [15,16]
- Transparency: There is widespread public concern about the kind of data acquired from users’ smartphones and its use by a variety of parties. There are two critical techniques for obtaining transparency. The first option is to create an ASCII text file of the app open. Because the imposed privacy and security features are frequently scrutinized by the research and academic community, using the app ASCII text file promotes transparency and confidence inside the system. Although this is a popular option, a public ASCII text file is not a cure-all for ensuring security. Several concerns originate from system setups and, as a result, the employment of a larger system that is not immediately evident from ASCII text file analysis. It could even be beneficial to make sure that the code is subjected to periodic review and trustworthy third-party audits.
While transparency may be a major factor in increasing end-user acceptance, it’s important to remember that any mobile app requires some level of confidence. This includes trusting the developers, the freelance check and verification team, the service operators and owners, and, most importantly, the businesses that provide critical parts such as mobile operating systems. [17, 18] Formalized paraphrase
FUTURE PATHWAYS:
The present COVID-19 situation has sparked a trend of using a virus-tracking app on a large scale. We may be better prepared for a virulent illness of this magnitude if these applications had been in place and thoroughly evaluated prior to the commencement of the pandemic. There has already been a frenzy of research activity throughout the world to build next-generation pursuit applications ready for urgent readiness should the world confront the same, or maybe even more severe epidemic. Next, we tend to consider various potential analytical directions.
When thinking about analysis areas for future tracing applications, it’s probably ideal to think about near-term development, say the next 5 years, with more “blue sky” sort of analysis pushed to the post-5-year horizon. In the short term, we believe that the following are important concerns. [19]
Improvement in proximity accuracy: We have discussed the current issues connected with proximity accuracy. Bluetooth technology was not created with position or proximity determination as a critical component of the planning process. However, the most current version of Bluetooth free in 2020 has more choices that may be relevant for next-generation apps. Furthermore, new “Bluetooth-like” protocols should be built with a focus on location/proximity services throughout the development phase. Antenna design should be a part of this strategy, allowing not just distance precision but also direction-finding. Indeed, Bluetooth five.1 includes direction-finding capabilities, but with limited precision. At the moment, no Covid19 tracking app includes such direction capabilities in their proximity analysis. As hardware technology advances and the sub-nanosecond temporal arrangement becomes frequent among devices, the usage of time-of-arrival measurements may even be utilized. Indeed, several smartphone manufacturers have expressed a desire to incorporate an ardent Ultra-Wideband (UWB) processor, especially with Bluetooth proximity analyses in mind. In comparison to Bluetooth’s modest information measurement (2MHz), UWB uses 500MHz, which will very certainly result in cm-type precision for proximity detection. Analysis of integrating radio information with diverse location data obtained from multiple sensors incorporated on the phone, such as location-designed wireless local area network, Enhanced-GPS, gyroscopes, accelerometers, and magnetometers, shows promise for improving proximity accuracy. These sensors can be powered by developments in software solutions such as the sophisticated digital procedures for location pursuit and artificial intelligence-based algorithms. One might envisage new “proximity” styles aimed precisely at integrating the required hardware, software, and protocol styles into a single chip.[20,21]
A completely localized design for infection tracing: one of the “takeaway messages” from the COVID-19 disaster is that privacy issues must be addressed for wider public usage. None of the apps we’ve described above are often thought of as having a wholly localized architecture – all of them employ a central server to varying degrees, sometimes under the direction of a governing authority. An investigation of a wholly localized system utilising some kind of peer-to-peer network to permit privacy-preserving data exchange amongst user devices should be conducted.
Artificial intelligence-based algorithms: AI algorithms square measure are increasingly being adopted as phone processing capacity improves. The use of such algorithms in assisting with infection risk decision-making is clear. The algorithms will become “active” in the sense that they will dynamically adapt and self-improve in their dependability and accuracy through measures such as real infection identification, lost detections, and false-positive results. We foresee a lot more investigation in this field, particularly with the combination of AI and hence localized design.
Analysis outcomes square measure more lasting to forecast in a post-5-year continuation. A lot is dependent on hardware development and the launch of new technologies that are square measure expected to hit the market. However, the most interesting of these emerging technologies may be found in the quantum arena.[22]
Many believe quantum computing is on the verge of a breakthrough in both development and commercialization. Future research on tracing solutions that make use of the significantly more powerful computational capabilities provided by quantum computing should begin now. These might include quantum-based artificial learning algorithms as well as improved Monte Carlo or particle filter sorting solutions. Data from phones will be routed to a central quantum computer for processing under this paradigm. Quantum sensing is another area of current research that is expected to make significant improvements in the next years. This technique uses hypersensitivity integrated in quantum traps to provide superior temporal order, network synchronization, measurement system precision, and site accuracy, to name a few applications. Clearly, some of these issues may be provided to the contact tracing arena to improve the performance and effectiveness of the applications. Quantum communications is the most advanced of all new quantum applications, at least in terms of preparation. Industrial offers in the quantum communications arena currently exist, and proof-of-principle preparation has already taken place in-house. The primary impact of this technology on tracing applications is the enhanced communications security and privacy safeguards it provides. In principle, if correctly implemented, future virus-tracking programs would have unconditional security and privacy– hacking and unauthorized access to virus-tracking knowledge will be rendered obsolete. [22,23]
CONCLUSION
The COVID-19 epidemic continues to have an impact on everyone’s way of life. Contact tracking applications have the potential to play a crucial role in assisting health officials in swiftly identify persons who have been exposed to the virus. The impending interest and acceptance of tracking app technology may increase health authorities’ tracing power; but, as this article has indicated, it is not a solution. Users, knowledge protection agencies, and researchers continue to raise concerns about these apps. The majority of difficulties are linked with user knowledge management, maybe non-trivial false positive and negative examples, and hence security and privacy issues with these apps. Radio-controlled by these issues, this text bestowed an outline of the 3 common tracing app architectures: centralized, suburbanized, and hybrid; and an outline of well-liked apps among these classes. Furthermore, the research focused on privacy and security, mapping attacks that may potentially be executed in any of the three designs. This statement also addresses another user’s concerns about battery depletion, compatibility, consent withdrawal, and transparency. Finally, we will discuss a few of the near future and future analytical directions.
We should emphasize that each architecture has advantages and disadvantages, as well as distinct attack models and defenses, implementation complexity, and operational costs. A government’s selection of a certain design is based on familiarity with technology and integration with current tracing systems. On the other hand, user adoption of an app is entirely elective. Users have legitimate concerns about the privacy and security of their PII obtained through these apps. [24] The adoption rate by users will be transparent, and the authorities will ensure statutory safeguards against the abuse of information coming from this system.
We additionally highlight that government agencies and service providers like ISPs, as well as large corporations like Apple/Google, are already tracking people by utilizing old apps and technologies like LAN connections, cell communication tower areas, GPS navigation apps, and a wide range of cameras deployed across cities. Since many users already install a myriad of apps on their phones or smart watches (games, social media, etc.) without understanding the security/privacy implications, the authors believe that installing a tracing app that primarily serves the noble purpose of keeping the community safe from spreading the COVID-19 illness should not cause undue concern. We believe that this text will help the research community understand various technological and cyber security issues of tracking apps, as well as assist users and agencies in creating an extra knowledge call for the voluntary adoption of an app available in their geographical areas.
REFERENCES:
- Ting, D. S. W., Carin, L., Dzau, V. & Wong, T. Y. Nat. Med.26, 459–461 (2020).
- Kahn, F. S. Tulane Law Rev.6, 1579–1644 (2002).
- Singer, N. & Choe, S.-H. The New York Times https://www.nytimes.com/2020/03/23/technology/coronavirus-surveillance-tracking-privacy.html (23 March 2020; updated 17 April 2020)
- The Economist https://www.economist.com/briefing/2020/03/26/countries-are-using-apps-and-data-networks-to-keep-tabs-on-the-pandemic (26 March 2020).
- European Data Protection Board. https://edpb.europa.eu/news/news/2020/statement-edpb-chair-processing-personal-data-context-covid-19-outbreak_en (16 March 2020).
- Lomas, N. TechCrunch https://techcrunch.com/2020/03/20/what-are-the-rules-wrapping-privacy-during-covid-19/ (2020).
- Hart, V. et al. Outpacing the Virus: Digital Response to Containing the Spread of COVID-19 while Mitigating Privacy Risks (Edmond J. Safra Center for Ethics, 2020).
- Sharma, T., Bashir, M. Use of apps in the COVID-19 response and the loss of privacy protection. Nat Med 26, 1165–1167 (2020). https://doi.org/10.1038/s41591-020-0928-y
- World Health Organization. WHO guideline: Recommendations on digital interventions for health system strengthening. Geneva: WHO; 2019.
- Mohanty B, Chughtai A, Rabhi F. Use of Mobile Apps for epidemic surveillance and response – Availability and gaps. Glob Biosecurity 2019; 1 : 37. Available from: https://jglobalbiosecurity.com/article/10.31646/gbio.39/, accessed on April 8, 2020.
- Bassi A, Arfin S, John O, Jha V. An overview of mobile applications (apps) to support the coronavirus disease 2019 response in India. Indian J Med Res 2020;151:468-7
- Roundup: Tech’s role in tracking, testing, treating COVID-19. Available from: https://www.mobihealthnews.com/news/ roundup-techs-role-tracking-testing-treating-covid-19, accessed on April 8, 2020.
- K. Michael, R. Abbas, Behind covid-19 contact trace apps: The googleapple partnership, IEEE Consumer Electronics Magazine 9 (5) (2020) 71–76.
- R. Abbas, K. Michael, Covid-19 contact trace app deployments: Learnings from australia and singapore, IEEE Consumer Electronics Magazine 9 (5) (2020) 65–70.
- Z. Huang, H. Guo, Y.-M. Lee, E. C. Ho, H. Ang, A. Chow, Performance of digital contact tracing tools for COVID-19 response in singapore: Cross-sectional study, JMIR mHealth and uHealth 8 (10)(2020) e23148. doi:10.2196/23148.URL https://doi.org/10.2196/23148
- S. Gupta, S. D. Langhans, S. Domisch, F. Fuso-Nerini, A. Fell¨ander, M. Battaglini, M. Tegmark, R. Vinuesa, Assessing whether artificial intelligence is an enabler or an inhibitor of sustainability at indicator level, Transportation Engineering 4 (2021) 100064
- C. T. Nguyen, Y. M. Saputra, N. Van Huynh, N. Nguyen, T. V. Khoa, B. M. Tuan, D. N. Nguyen, D. T. Hoang, T. X. Vu, E. Dutkiewicz, S. Chatzinotas, B. Ottersten, A comprehensive survey of enabling and emerging technologies for social distancingpart ii: Emerging technologies and open issues, IEEE Access 8 (2020) 154209–154236.
- N. Ahmed, R. A. Michelin, W. Xue, S. Ruj, R. Malaney, S. S. Kanhere, A. Seneviratne, W. Hu, H. Janicke, S. Jha, A survey of COVID-19 contact tracing apps, IEEE ACCESS 10.1109/ACCESS.2020.3010226 (2020) 134577–134601.
- I. Braithwaite, T. Callender, M. Bullock, R. W. Aldridge, Automated and partiallyautomated contact tracing: a rapid systematic review to inform the control of COVID19doi:10.1101/2020.05.27.20114447.URL https://doi.org/10.1101/2020.05.27.20114447
- C. T. Nguyen, Y. M. Saputra, N. Van Huynh, N. Nguyen, T. V. Khoa, B. M. Tuan, D. N. Nguyen, D. T. Hoang, T. X. Vu, E. Dutkiewicz, S. Chatzinotas, B. Ottersten, A comprehensive survey of enabling and emerging technologies for social distancingpart ii: Emerging technologies and open issues, IEEE Access 8 (2020) 154209–154236
- W. Taylor, Q. H. Abbasi, K. Dashtipour, S. Ansari, S. A. Shah, A. Khalid, M. A. Imran, A review of the state of the art in non-contact sensing for covid-19, Sensors 20 (19). URL https://www.mdpi.com/1424-8220/20/19/5665
- E. Aitenbichler, M. Muhlhauser, An ir local positioning system for smart items and devices, in: 23rd International Conference on Distributed Computing Systems Workshops, 2003. Proceedings., 2003, pp. 334–339
- A. Ferrari, E. Santus, D. Cirillo, M. P. de Leon, N. Marino, M. T. Ferretti, A. S. Chadha, N. Mavridis, A. Valencia, Simulating SARS-CoV-2 epidemics by region-specific variables and modeling contact tracing app containment, npj Digital Medicine 4 (1). doi:10.1038/s41746-020-00374-4. URL https://doi.org/10.1038/s41746-020-00374-4
- N. Ahmed et al., “A Survey of COVID-19 Contact Tracing Apps,” in IEEE Access, vol. 8, pp. 134577-134601, 2020, doi: 10.1109/ACCESS.2020.3010226 .increased significantly if complete
 Book a Demo to Build Your Team Today!
Book a Demo to Build Your Team Today!
 Read Case Studies
Read Case Studies 



 Virtual Medical Assistants
Virtual Medical Assistants



