Summarize this blog post with:
How We Avoided Healthcare Compliance Issues with Deep Encryption Vetting?
In the healthcare industry, safeguarding sensitive patient information is a top priority. With increasing regulatory pressures and the growing risk of data breaches, healthcare organizations must implement robust encryption protocols to ensure that confidential patient data is protected. One of the most effective strategies to avoid healthcare compliance issues is through deep encryption vetting, a comprehensive process that not only ensures data security but also helps healthcare organizations stay compliant with regulatory standards.
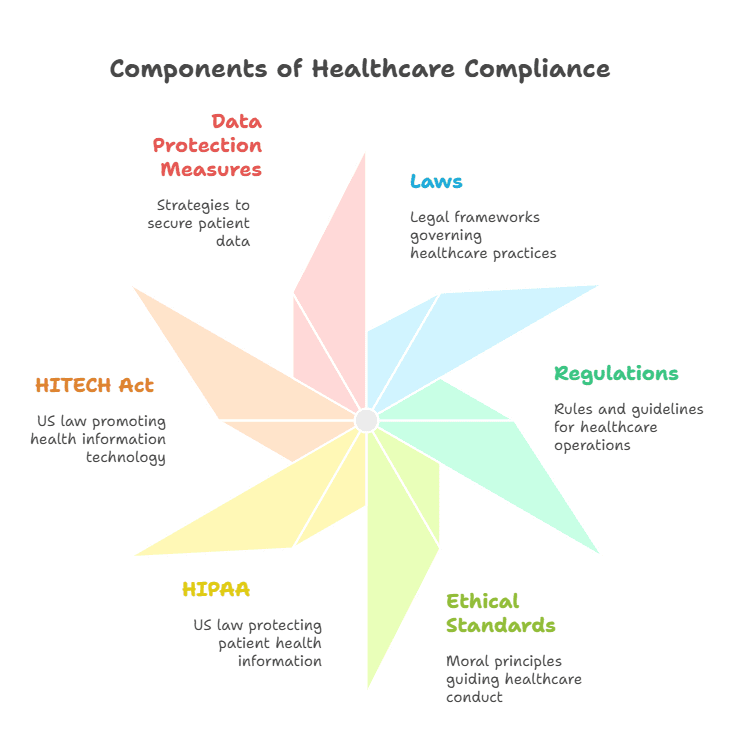
The Importance of Healthcare Compliance
Healthcare compliance refers to the adherence to various laws, regulations, and standards aimed at protecting patient data and ensuring ethical medical practices. The Health Insurance Portability and Accountability Act (HIPAA) in the United States, for example, mandates strict guidelines for the protection of patient health information. Failing to comply with these regulations can result in severe penalties, including hefty fines and reputational damage.
In addition to HIPAA, healthcare organizations must navigate a complex landscape of other laws, including the HITECH Act, which further strengthens the protection of health information in the digital age. With the rise of digital health records, telemedicine, and mobile health apps, the need for strong encryption has never been greater.
What is Deep Encryption Vetting?
Deep encryption vetting is a process of thoroughly testing and validating the encryption systems used to protect sensitive data. This process goes beyond basic encryption protocols to ensure that all potential vulnerabilities are addressed and that the encryption methods are robust enough to withstand evolving cybersecurity threats.
During deep encryption vetting, healthcare organizations assess the strength and integrity of encryption algorithms, encryption keys, and key management procedures. The vetting process includes rigorous testing to identify and mitigate any weaknesses that could compromise the security of patient data. Additionally, the encryption system is regularly updated to stay ahead of emerging threats, ensuring that the organization’s security infrastructure remains strong and compliant.
The Process of Deep Encryption Vetting
The deep encryption vetting process involves several critical steps to ensure that encryption systems are up to the task of protecting sensitive data:
-
Assessment of Encryption Algorithms: Reviewing the strength of the encryption algorithms used to secure patient data. Common algorithms like AES (Advanced Encryption Standard) and RSA are often tested for vulnerabilities.
-
Key Management Review: Ensuring that encryption keys are managed securely. Key management is one of the most critical aspects of encryption, as weak or mismanaged keys can compromise data security.
-
Penetration Testing: Performing simulated cyberattacks to identify potential vulnerabilities in the encryption system. This testing helps identify weaknesses that could be exploited by hackers.
-
Regular Updates: Ensuring that the encryption system is regularly updated to address new cybersecurity threats and vulnerabilities.
-
Compliance Audits: Conducting audits to ensure that the encryption system meets the requirements of applicable laws and regulations, including HIPAA, GDPR, and others.
How Deep Encryption Vetting Helps Avoid Compliance Issues?
1. Ensuring HIPAA Compliance
HIPAA mandates that healthcare organizations implement “reasonable and appropriate” safeguards to protect patient data. One of the most important safeguards is encryption. By vetting and using strong encryption methods, healthcare organizations can ensure that they meet HIPAA’s encryption requirements for both data at rest and data in transit.
Data at rest refers to data stored on a device or server, while data in transit refers to data being transmitted over a network. Both types of data are vulnerable to unauthorized access if not properly encrypted. Deep encryption vetting ensures that both aspects of patient data protection are thoroughly addressed, helping healthcare organizations avoid violations of HIPAA’s data security provisions.
2. Preventing Data Breaches
A single data breach can lead to severe financial penalties and irreparable damage to a healthcare organization’s reputation. Deep encryption vetting plays a crucial role in preventing data breaches by ensuring that all data, whether it’s patient health information or personal details, is fully protected with the highest level of encryption.
Encryption acts as a barrier to unauthorized access, ensuring that even if a cybercriminal gains access to a system, they cannot read or manipulate the data without the correct decryption key. Deep encryption vetting adds an extra layer of assurance by rigorously testing the encryption protocols to ensure that they remain secure under various scenarios.
3. Meeting Regulatory Requirements
Healthcare organizations must comply with a variety of regulations that govern the security of patient data. In addition to HIPAA, these may include the General Data Protection Regulation (GDPR) in the European Union or the California Consumer Privacy Act (CCPA) in California. Deep encryption vetting helps organizations meet the stringent data protection standards set by these regulations by ensuring that all patient data is encrypted to the highest standards.
By adopting encryption systems that meet or exceed the requirements of these regulations, healthcare organizations can avoid legal and financial penalties. Compliance is not only about meeting the minimum standards—it’s about proactively addressing potential risks and ensuring that the organization is well-prepared for audits and inspections.
4. Building Trust with Patients
Patient trust is crucial in the healthcare industry. Patients need to feel confident that their sensitive information is secure and that healthcare providers are taking every possible step to protect their data. By investing in deep encryption vetting, healthcare organizations demonstrate their commitment to safeguarding patient privacy and building long-term trust.
When patients trust that their personal and health information is being handled securely, they are more likely to engage with healthcare providers and share sensitive information necessary for their care. This trust is essential for fostering positive patient-provider relationships and enhancing the overall patient experience.

Key Benefits of Deep Encryption Vetting
-
Enhanced Security: Deep encryption vetting ensures that encryption algorithms are robust and up to date, reducing the risk of data breaches and unauthorized access.
-
Compliance Assurance: Through thorough testing, organizations can ensure they meet HIPAA and other regulatory standards, avoiding costly compliance violations.
-
Ongoing Protection: Regular vetting helps keep encryption systems ahead of emerging cybersecurity threats, ensuring continuous protection of patient data.
-
Reputation Management: By adopting best practices in encryption, healthcare organizations can protect their reputation and maintain patient trust.
-
Mitigation of Financial Risk: Avoiding penalties and fines associated with non-compliance or data breaches helps protect the organization’s financial health.
What Did We Learn?
In the healthcare industry, data security is non-negotiable. Deep encryption vetting provides healthcare organizations with a proactive, comprehensive approach to securing patient data and avoiding compliance issues. By thoroughly assessing encryption algorithms, managing encryption keys, and staying ahead of emerging threats, healthcare organizations can ensure that they remain compliant with regulations, prevent costly data breaches, and build trust with patients. Investing in deep encryption vetting is not only a way to protect sensitive information—it is also an essential step toward maintaining a strong reputation and ensuring long-term success in the healthcare sector.
What People Are Asking?
 Book a Demo to Build Your Team Today!
Book a Demo to Build Your Team Today!



 Read Case Studies
Read Case Studies 



 Virtual Medical Assistants
Virtual Medical Assistants



